Context
The company Chip&Fish has developed a new secure architecture called BattleChip. It has implemented a lightweight virtual machine (CHIP-8) and a secure element.
The secure element encrypts a message of size 10 with a session key.
It is also possible to ask the secure element to check whether a K key is the current session key.
The Chip&Fish company is asking you to test the robustness of their architecture. Your task is to find an attack to recover the current session key.
To interact with this new component, BattleChip implements the operation code
0000 and 0001 to interact with the encryption function and the verification function.
Assembly code for these two functions is supplied within the project.
The builder has also added the FFFF operation code to stop the CPU execution.
Here’s a schematic of the architecture:
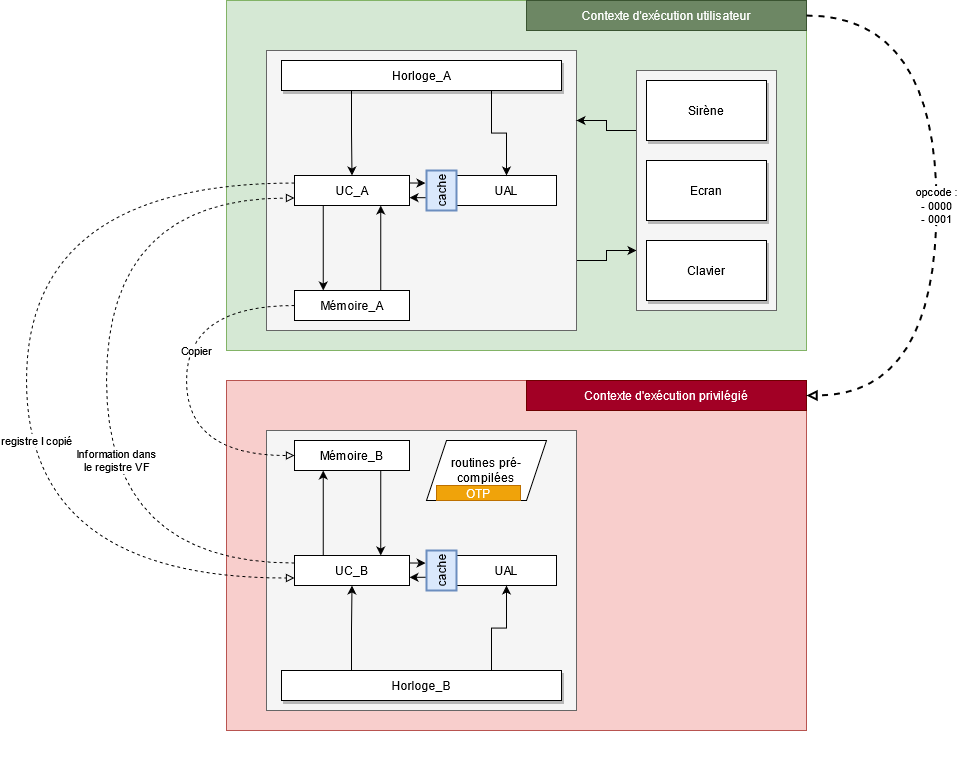
The manufacturer has also left a few notes about the peripherals:
--- Keyboard ---
No keyboard, no pong. No pong... no pong.
Using an operation code that requires interaction
the client will terminate program execution.
--- Clock ---
Nothing to declare, Captain.
--- Siren ---
For your listening pleasure, the siren makes no noise.
It is however connected.
--- Display ---
The screen sends ANSI characters to control the display.
A 64x32 or larger console is recommended.
or larger. The VM does not return any specific information
unless an error occurs during execution.
So make good use of the screen.
For Windows users, here’s a sample code to enable support for ANSI characters:
# Windows user ONLY
import os
import win32api
import ctypes
def activate_vti():
"""Enable Virtual Terminal Input
Documentation: https://docs.microsoft.com/en-us/windows/console/setconsolemode
"""
if os.name == "nt":
kernel32 = ctypes.windll.kernel32
hStdout = win32api.GetStdHandle(win32api.STD_OUTPUT_HANDLE)
result = kernel32.SetConsoleMode(hStdout, 0x1 | 0x2 | 0x4)
if result == 0:
raise RuntimeError("Console doesn't support ANSI character")