Description
Hello,
According to our analysis coupled with our satellite photos, we have confirmation that the target, while claiming being a vaccine production plant, is in reality a toxic liquid production plant used for military purposes.
A preliminary network analysis indicates that the target is controlled by a programmable logic controller, itself communicating via a SCADA interface by the OPC-UA protocol in binary mode. We have exposed the target on the Internet using a UMTS implant, and it is now accessible on the network:
localhost:4841
Here is a screenshot of the SCADA interface at an unknown time:
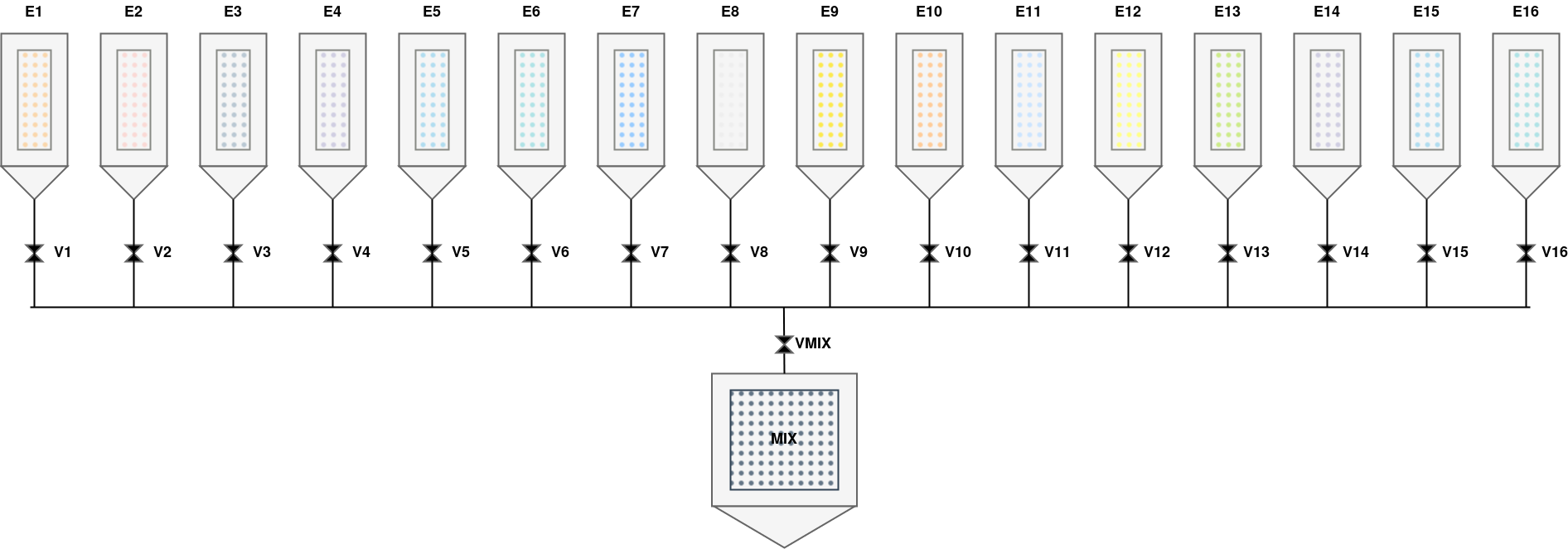
Some stolen engineering documents showed that the toxic liquid formula is composed of 16 elements. We do not know the quantities used in the formula and the order of the different elements: your goal is to recover them.
It seems that the elements are added to the `MIX’ tank (at the bottom of the screenshot) two by two, but to create an effective antidote, we need to know exactly in which order and with which quantities the couples of elements are mixed.
Hurry up, time is running out…
Note: The number of elements in a pair of elements should be given in increasing order (030c and not 0c03 in Step 2 of the example below), and the corresponding quantities in the same order.
Example: We provide an example of the flag format. Assume that the manufacturing process has the following three steps:
- Step 1: Add 27 units (
0x1b) of element 1 (0x01) and 47 units (0x2f) of element 8 (0x08) to theMIXtank. - Step 2: Add 95 units (
0x5f) of element 12 (0x0c) and 141 units (0x8d) of element 3 (0x03) to theMIXtank. - Step 3: Add 230 units (
0xe6) of element 5 (0x05) and 177 units (0xb1) of element 16 (0x10) to theMIXtank.
The flag to submit would be FCSC{01081b2f030c8d5f0510e6b1}, where all values are represented in hexadecimal notation.
Files
Author

Challenge Instructions
- First, download docker-compose.yml:
curl https://hackropole.fr/challenges/fcsc2023-misc-evil-plant/docker-compose.public.yml -o docker-compose.yml - Launch the challenge by executing in the same folder:
docker compose up - Access the challenge at localhost:4841 (OPC-UA protocol).
In case you encounter problems, please consult the FAQ.
Flag
Submit your solution
You can submit your writeup for this challenge. Read the FAQ to learn how to proceed.
You need to be logged in to submit a writeup.