Description
The MegaSecure company has just released a security update for their servers. After analyzing the update, you notice that the editor now uses this code for exponentiation:
unsigned long exp_by_squaring(unsigned long x, unsigned long n) {
// n is the secret exponent
if (n == 0) {
return 1;
} else if (n % 2 == 0) {
return exp_by_squaring(x * x, n / 2);
} else {
return x * exp_by_squaring(x * x, (n - 1) / 2);
}
}
You have access to a server on which you can run as a user
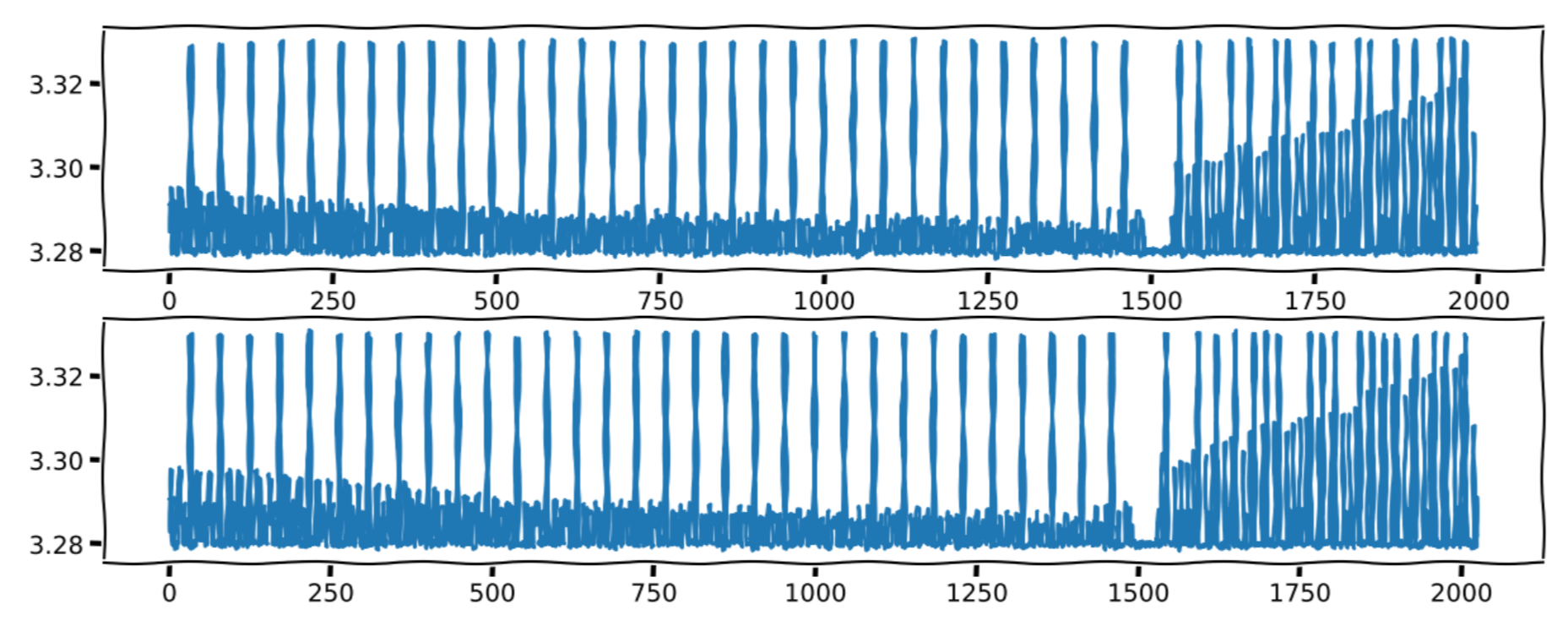
exp_by_squaring(2, 2727955623) while measuring its power consumption.
The exponent here is therefore n = 2727955623, or 10100010100110010100110010100111
in binary.
This consumption trace is saved in user_trace.csv.
You have also managed to measure the energy consumption during
exponentiation of an administrator data.
This consumption trace is saved in trace_admin.csv.
Can you find its secret exponent n?
The flag is in FCSC{1234567890} format with 1234567890 to be replaced by
the secret exponent of the administrator written in decimal.
Files
-
spanosaurus.png
443.82 KiB – ef780dd44732fdda38eae0bb7b0ca30a102574d65fe1a53cec914d0cf2a2bc11 -
trace_admin.csv
49.44 KiB – 4f7d8dd8d0372379f25b912ad38b6bc58acec447ae235c93e8e6664005875751 -
trace_utilisateur.csv
48.78 KiB – 7e5790762ceaa274aa8e72cf70b6770eb798cd43d02e477003b519e2ac476004
Author

Flag
Submit your solution
You can submit your writeup for this challenge. Read the FAQ to learn how to proceed.
You need to be logged in to submit a writeup.