Description
General Context:
You have recovered a box that protects secure communications with satellites, taking advantage of a poorly protected access to the sensitive premises of the company that operates them. Controlling this equipment would allow you to intercept and decrypt these communications.
Unfortunately, the designers of the box considered theft into their threat model: the machine will not boot up until a password is provided via the exposed UART serial interface. After a few unsuccessful attempts or too much time without seeing the correct password, the entire system (including the keys) is erased.
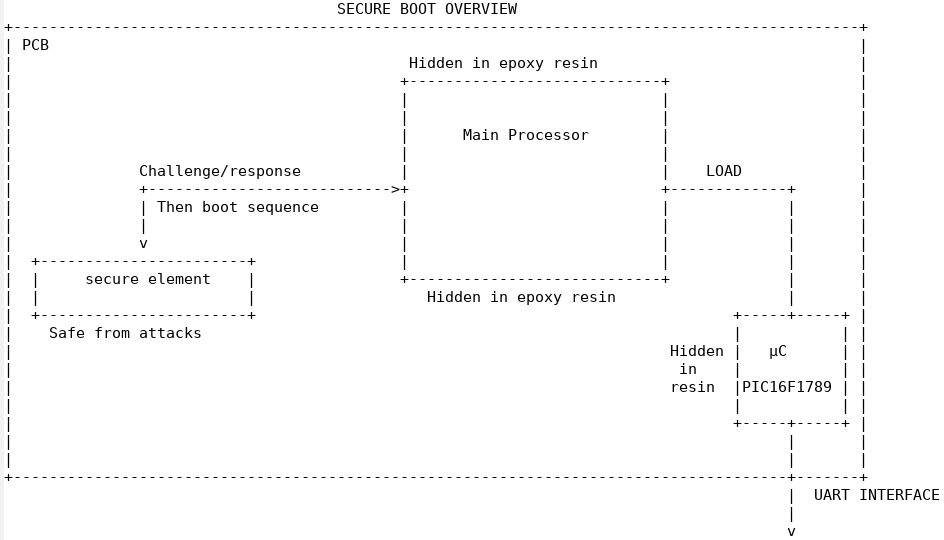
Anyway, let’s start intrusive work on the motherboard PCB and let’s dump flash memories and other disks! Unfortunately, when you open the case, you discover that a secure boot seems to have been used. Indeed, a secure component with a smart card reference is inserted into a micro-SIM slot, and the rest of the components are embedded in epoxy resin, so they are difficult to access.
Thanks to a few pages of leaked datasheet (see schema.png), you understand that a main processor boots on its internal flash, communicates with the smart card, authenticates it via a challenge/response mechanism, and finally loads a microcontroller connected to the UART which waits for the unlocking password.
Challenge Context:
Since the communication bus with the secure component is the only accessible part without resin (the component is in QFP format allowing easy soldering of wires), you decide to try your luck by connecting your logic analyzer to the four tracks that seem to connect it to the processor.
After several observations, the challenge/response part seems random and not very usable.
The second part is more intriguing: it seems to change from one boot to another, but you recognize some patterns.
So you focus on this part, save two captures, and the detailed analysis with your Sigrok and gtkwave softwares starts…
Note: There is a follow-up challenge available here: Smarboot 2.
Files
-
schema.png
23.13 KiB – dd7acbbf24fd89ab98ff745c0502808915becd47bd3a77e10f7dfadc109a0072 -
capture1.vcd.7z
25.55 MiB – 8c2d220a6c4a7b3612bbca5078c8e650c3d6827d7931fc544d418103dd129d7f -
capture2.vcd.7z
22.06 MiB – d8a33ddc8efc9bf5021a91cc673b956fde24e982cc6324ce2f4ec28709eafa4c
Author

Flag
Submit your solution
You can submit your writeup for this challenge. Read the FAQ to learn how to proceed.
You need to be logged in to submit a writeup.
Writeups
There are no public solutions for this challenge yet, but you can submit yours after getting the flag.